In this blog, we are going to look at what Authentication and Authorization and how they work on Kubernetes.
In simple terms, Authentication is letting you in on the Cluster and Authorization is what are the things you can do in the Cluster.
What is Authentication on Kubernetes?
The Authentication process initially begins with the API Server because when you type and enter a command, for example, kubectl create, the request first goes to the API Server.
The API Server endpoint always exposes its endpoint to users and services to communicate.
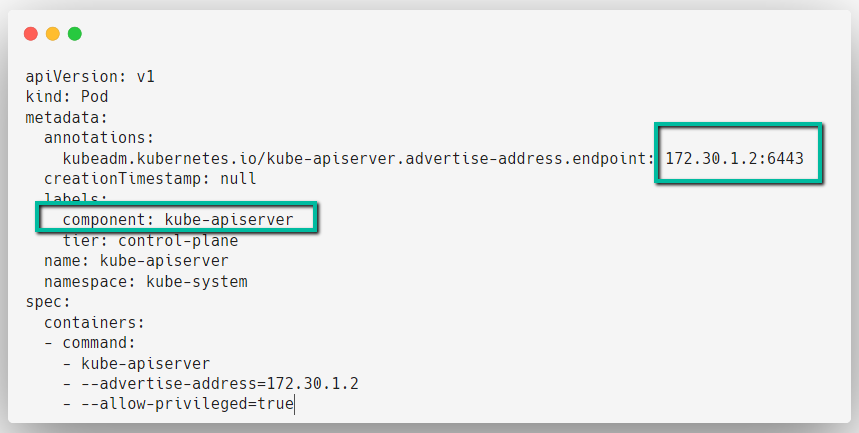
But how the API Server can know that the request came from an authorized user?
Let me show you an example of making an API call to the endpoint to list the Namespaces of the cluster using curl command.
curl https://172.30.1.2:6443/api/v1/namespaces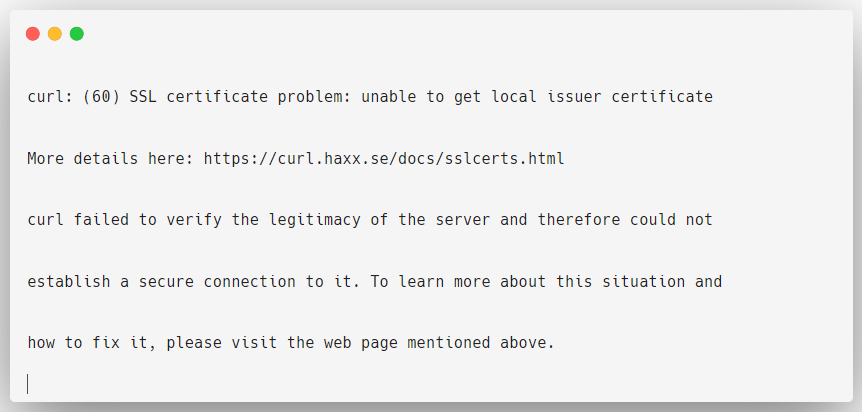
This is because we haven't provided any authentication details about the user who is making the curl request so the API Server rejects the request.
To get authenticated, we have various options available such as Token, Certificates and Identity Providers such as OIDC, LDAP, etc.
For testing purposes, I am taking the admin certificates from the /etc/kubernetes/admin.conf kubeconfig file.
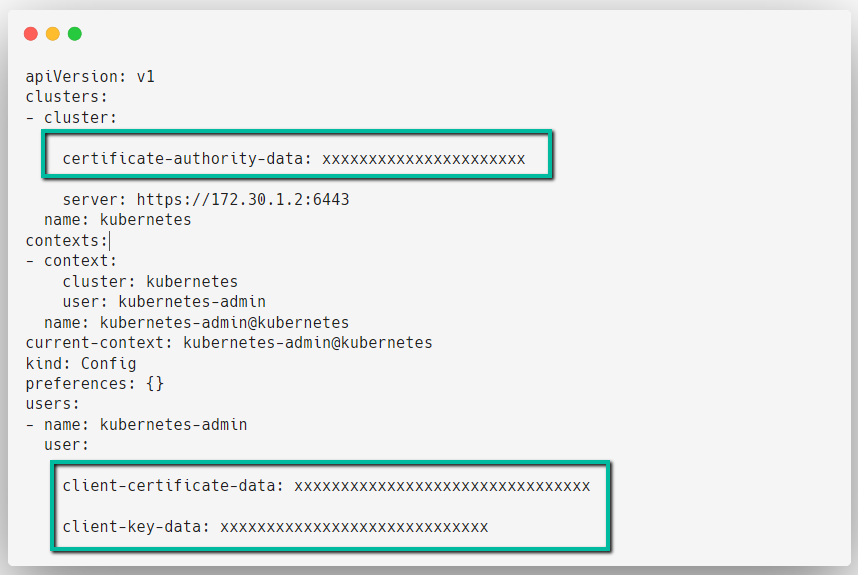
Creating environment variables with the values.
CLIENT=XXXXXXXXXXXXXXXXXXXXXX
KEY=XXXXXXXXXXXXXXXXXXXXXXXX
CA=XXXXXXXXXXXXXXXXXXXXXXXEncoding the values using the base64 mechanism.
echo $CLIENT | base64 -d - > client.pem
echo $KEY | base64 -d - > client-key.pem
echo $CA | base64 -d - > ca.pemNow, we can try again and see the result.
curl --cert client.pem --key client-key.pem --cacert ca.pem https://172.30.1.2:6443/api/v1/namespaces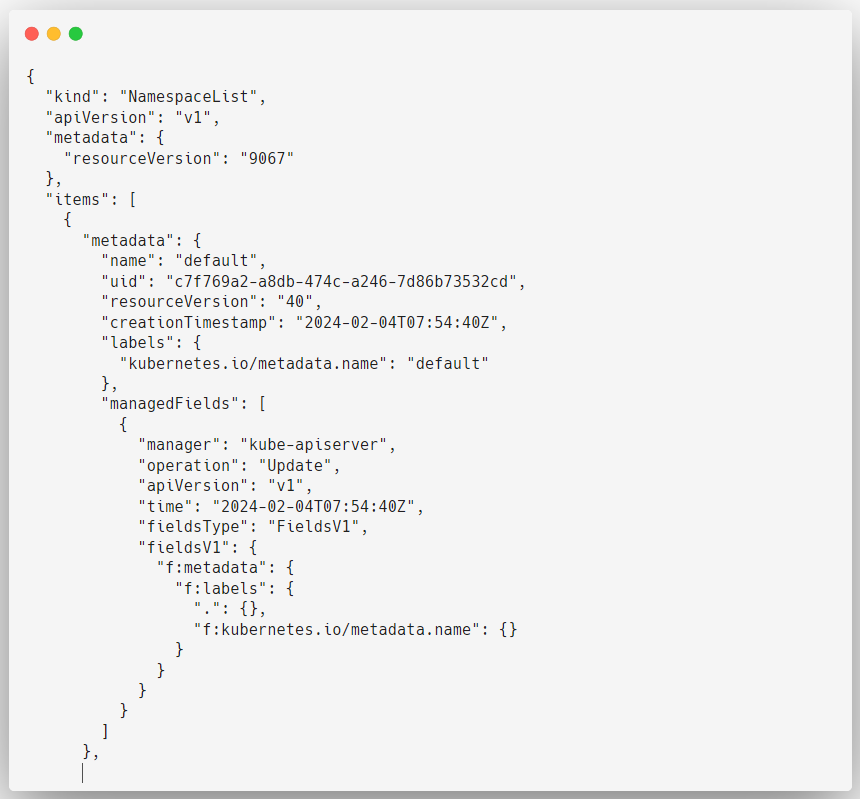
This time we are getting the response through the certificates and Kubernetes supports many methods to Authenticate with the Cluster.
What is Authorization on Kubernetes?
Authentication only helps you to prove your identity but that doesn't mean that you can do any actions on the Kubernetes cluster.
For example, if you want to create a Pod using kubectl run pod command, you need to be Authorized to perform this action.
For Authorization, different methods are available such as Node, ABAC, RBAC and Webhook.
Node Authorization: This Authorization is enabled by default because this gives permission to the Kubelet to access the Nodes, Pods and other objects.
ABAC Authorization: Through policies, we can perform Authorization and this method is disabled by default.
If you want to enable it, you need to modify the /etc/kubernetes/manifests/kube-apiserver.yaml manifest.
RBAC Authorization: Role-Based Access Control is one of the common Authorization methods on Kubernetes and it is enabled by default.
In this, we will create a Service Account and attach permission with that, when we attach the Service Account to a Pod, the Pod will get permission to access the resources.
Webhook Authorization: This is the remote API server Authorization method, through webhook this Authorization is possible.
